The Zero-Trust Approach to Healthcare Data Security: A Complete Guide
In an era where customer data is both vital and highly sought after, organizations must prioritize its protection more than ever. The healthcare sector, in particular, faces significant risks as its data is particularly vulnerable and often targets for cybercriminals. These offenders can profit handsomely by selling stolen healthcare information, making healthcare data security a critical concern.
The American Hospital Association (AHA) strongly advises senior hospital leaders to view cybersecurity as a strategic priority that should be deeply integrated into the organization’s governance, risk management, and business continuity frameworks. The reason is clear: a breach in data security doesn’t just compromise information—it can delay treatments, disrupt hospital operations, and even put patient lives at risk.
In this blog, we’ll explore how the Zero-Trust Architecture Model offers a transformative approach to healthcare data security.
Key Takeaways:
With rising healthcare data security breaches and ransomware attacks, Zero Trust has become a strategic priority, not just a security option. It shifts the focus from perimeter-based security to continuous verification of all users, devices, and applications—regardless of location.
According to IBM’s 2024 report, the healthcare sector faces the highest average cost of data breaches at $9.77 million per incident, highlighting the urgent need for robust healthcare data security measures beyond traditional frameworks.
The increasing use of telehealth, remote care models, and IoT medical devices dissolves traditional network boundaries, making patient data more vulnerable. Patient health records (PHRs) are now 10x more valuable on the dark web than credit card information, emphasizing the need for stringent healthcare data security standards.
Cloud technologies like Identity as a Service (IDaaS), end-to-end encryption, and automated compliance tools are critical for Zero Trust. They simplify secure access, protect data in transit and at rest, and ensure continuous regulatory compliance, especially with HIPAA and GDPR.
AI-powered security systems proactively detect threats, predict potential breaches, and automate responses. They are especially effective in identifying insider threats, flagging suspicious behavior, and mitigating risks in real time.
Key Data Breach Statistics:
In April 2024, National Public Data, a data broker specializing in background checks, suffered a massive breach affecting approximately 2.9 billion records. The compromised data included sensitive information such as Social Security numbers, names, and contact details, potentially impacting nearly all Americans.
In July 2024, AT&T experienced a significant data breach when hackers accessed its third-party cloud service provider, Snowflake. The breach affected nearly all of AT&T's wireless customers, exposing call logs, text message details, and personal information.
Approximately 74% of all data breaches in 2024 involved the human element, including social engineering attacks, errors, or misuse, emphasizing the need for enhanced employee training and awareness programs.
These staggering figures highlight the financial, operational, and reputational risks associated with inadequate healthcare data security approaches. Moreover, the rise of ransomware attacks targeting hospitals and healthcare systems adds another layer of complexity, compromising not just data but patient care itself.
What is Zero Trust Architecture, and Why is it Gaining Traction in Healthcare?
Zero Trust is a cybersecurity framework based on the principle of:
“Never trust, always verify.”
Unlike traditional security models that assume users inside the network are trustworthy, Zero Trust assumes that threats can come from anywhere—inside or outside the organization. It requires continuous verification of all users, devices, and applications, regardless of their location.
Why Healthcare Data Security Needs Zero Trust:
Data Sensitivity
Patient health records (PHRs) are 10 times more valuable on the dark web than credit card information.
Remote Care Models
The rise of telehealth and remote work has dissolved traditional network perimeters.
Regulatory Pressure
Compliance with HIPAA, GDPR, and HITECH demands stricter data access controls.
IoT and Connected Devices
Hospitals are filled with connected devices that can be exploited if not properly secured.
In 2023, 61% of organizations had a zero-trust initiative in place, up from just 24% two years earlier, according to a global Okta survey of information security decision-makers. In 2024, over 41% of technology and security professionals say they are in the advanced stage of zero-trust implementation, while 12% say they have achieved optimal maturity, according to a recent CDW survey of over 950 respondents.
Pillars of Zero Trust: The U.S. Cybersecurity Framework
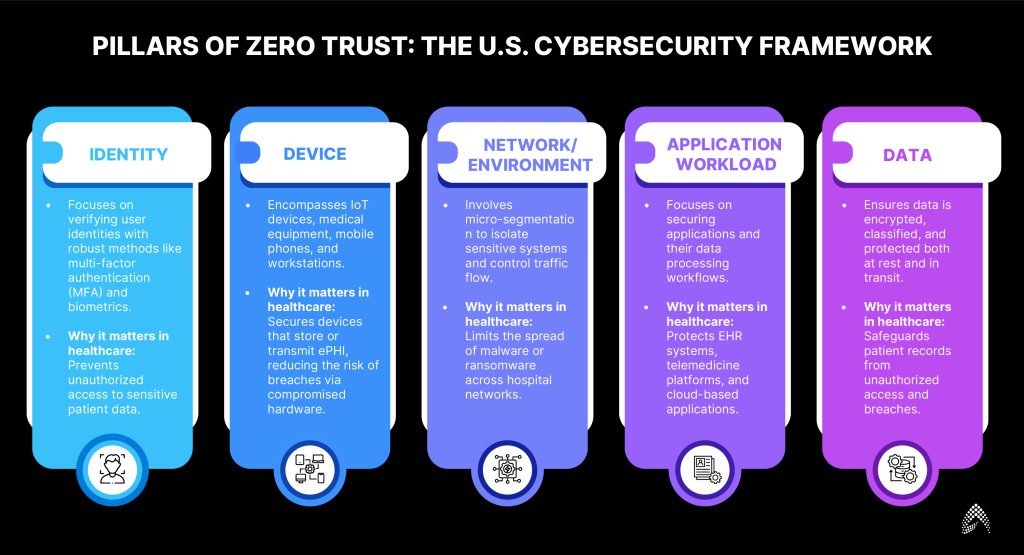
The U.S. Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency (CISA) has outlined five core pillars of the Zero Trust Maturity Model, offering guidance for organizations to build a Zero-Trust architecture for healthcare data security:
1. Identity:
Focuses on verifying user identities with robust methods like multi-factor authentication (MFA) and biometrics.
Why it matters in healthcare data security: Prevents unauthorized access to sensitive patient data.
2. Device:
Encompasses IoT devices, medical equipment, mobile phones, and workstations.
Why it matters in healthcare: Secures devices that store or transmit ePHI, reducing the risk of breaches via compromised hardware.
3. Network/Environment:
Involves micro-segmentation to isolate sensitive systems and control traffic flow.
Why it matters in healthcare: Limits the spread of malware or ransomware across hospital networks.
4. Application Workload:
Focuses on securing applications and their data processing workflows.
Why it matters in healthcare: Protects EHR systems, telemedicine platforms, and cloud-based applications.
5. Data:
Ensures data is encrypted, classified, and protected both at rest and in transit.
Why it matters in healthcare data security: Safeguards patient records from unauthorized access and breaches.
Steps Toward Healthcare Data Security: Zero Trust Architecture Implementation Guide
Here’s an actionable, step-by-step guide to help healthcare organizations successfully implement Zero Trust Architecture (ZTA) while enhancing patient data protection, ensuring regulatory compliance, and maintaining operational efficiency.
1. Assess Your Current Security Posture
Before implementing Zero Trust, conduct a comprehensive security audit to identify vulnerabilities in networks, applications, devices, and data storage systems.
Risk Assessment
Prioritize high-risk areas like EHRs, telehealth platforms, and IoT devices to identify potential external and insider threats.
Security Maturity Assessment
Use frameworks like NIST’s Cybersecurity Framework or CISA’s Zero Trust Maturity Model to evaluate your current security posture.
2. Define a Clear Zero Trust Strategy
A successful Zero Trust approach in healthcare requires a well-defined strategy aligned with your organization’s goals.
Align with Business Objectives
Focus on patient privacy, regulatory compliance, and cyber resilience
Establish Governance
Create a Zero Trust steering committee with IT leaders, CISOs, and clinical stakeholders to guide implementation.
Prioritize Critical Assets
Identify “crown jewels” like PHI, financial records, and medical research data for heightened protection.
3. Strengthen Identity & Access Management (IAM)
In the healthcare data security Zero Trust model, identity is the new perimeter. Ensure that access is based on verified identity, not just network location.
Multi-Factor Authentication (MFA)
Require at least two verification methods, like passwords plus biometrics.
Role-Based Access Control (RBAC)
Grant access based on job roles to minimize unnecessary data exposure.
Continuous Identity Verification
Monitor user behavior for anomalies, even after login, to detect suspicious activities.
4. Segment Networks (Micro-Segmentation)
For better healthcare data security, reduce the attack surface by isolating critical systems into smaller network segments with strict access controls.
Isolate Critical Applications
Segregate systems like EHRs, medical devices, and payment platforms.
Network Access Control (NAC)
Control which devices connect to specific segments based on their security status.
Dynamic Access Policies
Apply context-based rules, like additional verification for remote access.
5. Automate Threat Response
Speed is critical in healthcare data security. Automate security processes to detect and respond to incidents instantly.
Security Orchestration, Automation, and Response (SOAR)
Use platforms like Palo Alto Cortex XSOAR to automate threat detection and response.
Incident Playbooks
Develop predefined response strategies for threats like ransomware—automatically isolate compromised devices and trigger alerts.
Automated Compliance Reporting
Generate real-time reports to meet HIPAA and GDPR requirements efficiently.
How to Modernize Healthcare Security with Zero Trust: The Role of Cloud Services
As healthcare organizations continue to embrace digital transformation, the integration of cloud services has become indispensable for modernizing operations, improving patient care, and ensuring the scalability of health IT systems. However, with this shift comes an increased risk of cyber threats, data breaches, and compliance violations. This is where the Zero Trust Security Model, reinforced by advanced cloud services, emerges as the key to safeguarding healthcare data security.
1. Identity as a Service (IDaaS): Simplifying Secure Access
Managing user identities across multiple systems is complex, especially with remote staff, telehealth platforms, and third-party vendors. Identity as a Service (IDaaS) solutions like Okta and Azure Active Directory streamline this by providing cloud-based identity management that integrates seamlessly with both on-premises and cloud environments.
Key Features:
Multi-Factor Authentication (MFA)
Adds an extra layer of security beyond passwords.
Single Sign-On (SSO)
Simplifies secure access to multiple applications.
Adaptive Access Controls
Continuously monitors user behavior, flagging suspicious activities.
2. Data Encryption: Protecting Information in Transit and at Rest
Data encryption is the foundation of healthcare data security, especially for Protected Health Information (PHI). In a zero-trust environment, encryption ensures that even if data is intercepted, it remains unreadable without proper decryption keys.
Cloud services provide:
End-to-End Encryption
Protects data in transit (during transmission) and at rest (when stored).
Key Management Services (KMS)
Securely handles encryption keys for controlled access.
This is critical for safeguarding data shared through telehealth platforms, remote monitoring devices, and cloud-based EHR systems.
3. Automated Compliance Tools: Ensuring Continuous Regulatory Adherence
Healthcare organizations must comply with strict regulations like HIPAA, GDPR, and the HITECH Act. Manual compliance processes can be time-consuming and error-prone, especially in complex IT environments.
Cloud platforms offer automated compliance tools that:
Monitor Data in Real-Time
Quickly identify potential compliance violations.
Automate Risk Assessments
Detect vulnerabilities before they become threats.
Simplify Reporting
Platforms like AWS Compliance Center and Microsoft Compliance Manager provide pre-configured templates for regulatory audits.
This ensures continuous regulatory compliance while reducing administrative overhead.
The Role of Cloud Security in Ensuring Zero Trust in Healthcare
While cloud services provide the infrastructure to implement Zero Trust, cloud security solutions are the mechanisms that ensure it functions effectively. These solutions help healthcare organizations monitor, control, and secure data across complex, multi-cloud environments where traditional security measures often fall short.
1. Cloud Access Security Brokers (CASBs): Enforcing Data Governance Across Cloud Applications
CASBs act as a bridge between healthcare organizations and cloud applications, offering real-time visibility into how data is accessed and shared. They enforce access controls to ensure that only authorized users can interact with sensitive information, detect unauthorized apps (shadow IT), and apply Data Loss Prevention (DLP) policies to prevent accidental or malicious data leaks. CASBs are crucial for securing data in remote work settings and across personal devices, maintaining compliance with healthcare regulations like HIPAA.
2. Encryption and Tokenization: Advanced Data Protection for Multi-Cloud Environments
In a Zero Trust framework, encryption and tokenization provide robust protection for Protected Health Information (PHI). Encryption converts sensitive data into unreadable code, safeguarding it during transmission and storage. Tokenization replaces sensitive data with non-sensitive placeholders (tokens), ensuring that even if data is breached, it remains useless without the corresponding mapping system. Together, these techniques secure data across EHR systems, billing platforms, and multi-cloud environments.
3. AI-Driven Threat Detection: Proactive Security for Real-Time Threat Mitigation
AI-driven threat detection leverages machine learning to analyze large volumes of data, identifying suspicious behavior and potential threats in real time. AI can predict breaches, detect insider threats (e.g., unusual data access patterns), and automate responses like isolating compromised devices or revoking access. This proactive approach significantly reduces response times, helping healthcare organizations contain threats before they escalate.
Future Trends of Zero Trust in Healthcare
As technology evolves, so does the Zero Trust model. Here’s a glimpse into how Zero Trust is expected to shape the future of healthcare data security:
1. AI-Powered Security: Predictive Threat Analysis for Proactive Defense
The future of Zero Trust lies in predictive security, where AI doesn’t just detect threats—it anticipates them. Machine learning algorithms will analyze historical data to identify patterns that indicate potential vulnerabilities, allowing organizations to address security risks before they are exploited.
This shift from reactive to proactive security will be crucial in healthcare data security, where the cost of a breach can be measured not just in dollars, but in patient outcomes.
2. Zero Trust for IoT: Securing Medical Devices in Connected Healthcare Environments
The rise of Internet of Medical Things (IoMT) devices—such as smart infusion pumps, remote patient monitors, and connected imaging systems—introduces new vulnerabilities. Many of these devices were not designed with security in mind, making them easy targets for attackers.
Zero Trust principles are being adapted to secure these devices by:
Authenticating every device before allowing network access
Segmenting IoT devices from critical healthcare systems
Continuously monitoring device behavior for anomalies
This ensures that even if one device is compromised, it cannot be used as a gateway to access the broader network.
3. Decentralized Identity Verification: Leveraging Blockchain for Secure Access Management
Blockchain technology is poised to revolutionize identity management in healthcare. By creating decentralized, tamper-proof identity records, blockchain can eliminate the risks associated with traditional, centralized identity systems.
In a Zero Trust model, blockchain enables:
Secure, verifiable digital identities for patients, clinicians, and devices
Immutable audit trails for compliance and security investigations
Reduced reliance on third-party identity providers, minimizing potential attack vectors
This approach aligns perfectly with Zero Trust’s goal of ensuring that every access request is verified, authenticated, and authorized—without relying on implicit trust.
Conclusion: The Future of Healthcare Security is Zero Trust
As healthcare organizations face growing threats from ransomware, data breaches, and insider threats, the need for a proactive, resilient security model has never been greater. Zero Trust, supported by cloud services and AI-driven security solutions, offers a comprehensive framework to protect sensitive data, ensure regulatory compliance, and maintain patient trust.
Ready to modernize your healthcare security with Zero Trust? Contact us today to learn how our AI strategy and consulting services can help your organization implement a secure, scalable, and compliant Zero Trust architecture tailored to your unique needs.

Director – Global Delivery




